How to conduct a website security audit to prevent a cyberattack

Imagine you own a successful website. Business is booming and you’re on track to achieve your goals. Then one day, you find that your site’s security is compromised, putting your customer data and important business information at risk of unauthorized access. Your brand’s reputation and the trust you built over the years are at stake.
According to IBM’s Cost of a Data Breach Report, the global average cost of a data breach is $4.88 million — a 10% increase from the previous year. From online shops to global conglomerates, businesses are facing serious consequences from data breaches.
Fortunately, a devastating cybersecurity attack can be avoided.
You can easily identify security vulnerabilities and fix issues through a scheduled audit. Many think of a website security audit as yet another task on their to-do list. However, it’s your first line of defense against cybersecurity threats. Think of it as like carrying out a health checkup for your site. It helps you identify potential security issues before they become critical problems.
We created this guide to discuss essential components of a website security audit and provide you with best practices to avoid a breach.
9 top tools for your website security audit
Before we dive into the best practices for conducting a website security audit, let’s talk about the tools through which you can strengthen your website security.
1. Password manager solution
One of the reasons people don’t pick strong passwords is that they’re tough to remember. Hence, they often choose a password that’s easy to recall, such as their phone numbers, date of birth, pet name, maiden name, and so on.
An easy fix to this problem is to use a password manager. A password manager enables you to generate and store complex passwords for your accounts.
When it comes to protecting your website from unauthorized access, it’s best that you keep changing its password. You must ensure that you pick a unique combination of numbers and special characters each time.
Remembering complex passwords that you are to change constantly may not be easy. So, leveraging a password manager solution may come in handy.
2. Website backup solution
A reliable backup solution is essential for data protection. We’re all susceptible to the risk of data loss. A backup solution comes in handy here, allowing you to recover everything important.

A backup solution ensures your website security by saving a copy of all your files and configurations. You don’t have to start building a website from scratch in case a security incident or technical failure leads to data loss. You already have a backup. So you can easily restore everything you need to keep your site up and running again.
With EasyWP, you can take advantage of the one-click backup feature right from your dashboard, making it quick and effortless to secure your site’s data. This built-in solution ensures that your latest configurations, files, and content are always just one click away from restoration if anything goes wrong.
3. Security plugin
Installing a security plugin may significantly improve your website security. A reliable security plugin comes with essential information protection capabilities, which serve as a vanguard against malware and information infiltration risks.
With the help of a security plugin, you can actively monitor your website for suspicious activities and block malicious attempts from cybercriminals. You should never underestimate the significance of a security plugin. It’s one of the essential installations you must consider when starting your journey as a website owner.
4. SSL certificate
Installing an SSL certificate is important for your website’s security. It encrypts the connection between your website and its visitors. It ensures that no unauthorized person can access your website data during transmission. So, it encrypts sensitive information into a complex code.
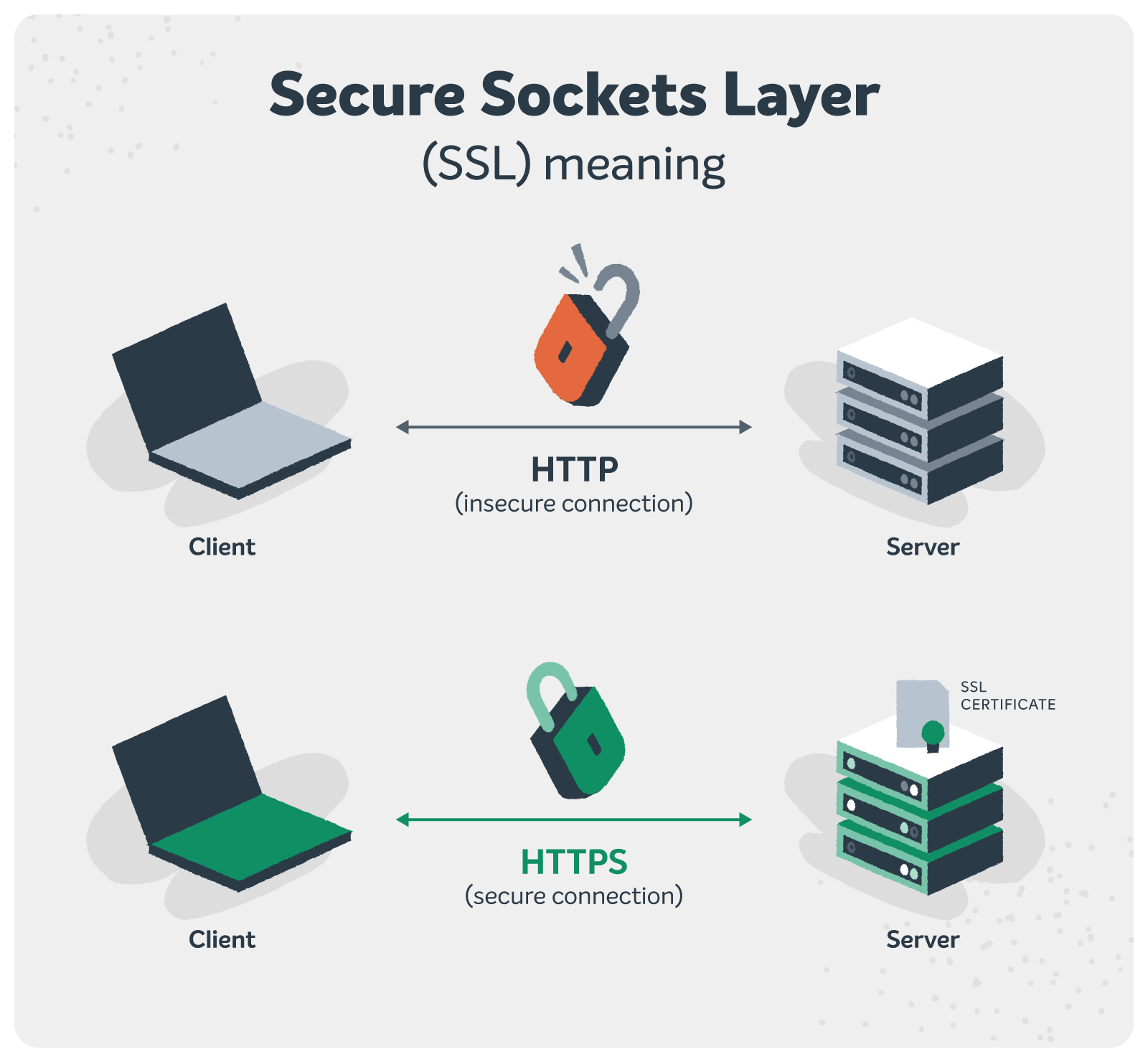
The benefit of this is that even though your website’s security is compromised and cybercriminals have access to your information, they won’t be able to make any sense of it. Be it your login credentials, your customers’ credit card details, or any other sensitive information, everything will be encrypted.
Installing an SSL certificate also complements your search engine rankings. Search engines prefer recommending secure HTTPS websites compared to the ones with non-secure connections.
5. Web application firewall (WAF)
A web application firewall assesses and filters your traffic in real time. They distinguish legitimate requests from malicious ones and prevent potential attacks. WAFs help you counter threats, such as SQL injection, cross-site scripting (XSS), and file inclusion exploits.
Reliable WAF solutions leverage machine learning algorithms to evolve. They continuously learn from global threat intelligence networks and keep updating their mechanisms, protecting you from newly discovered cyberattacks.
So, they keep your website secure from known and emerging vulnerabilities. They provide you with detailed reports, which help you fine-tune your security settings as per your needs.
6. Vulnerability scanner
You need a vulnerability scanner to check your website’s potential weaknesses. Reliable vulnerability scanners check for outdated software versions, AI cybersecurity risks, weak authentication systems, SQL injection points, and many other potential issues with your website’s security.
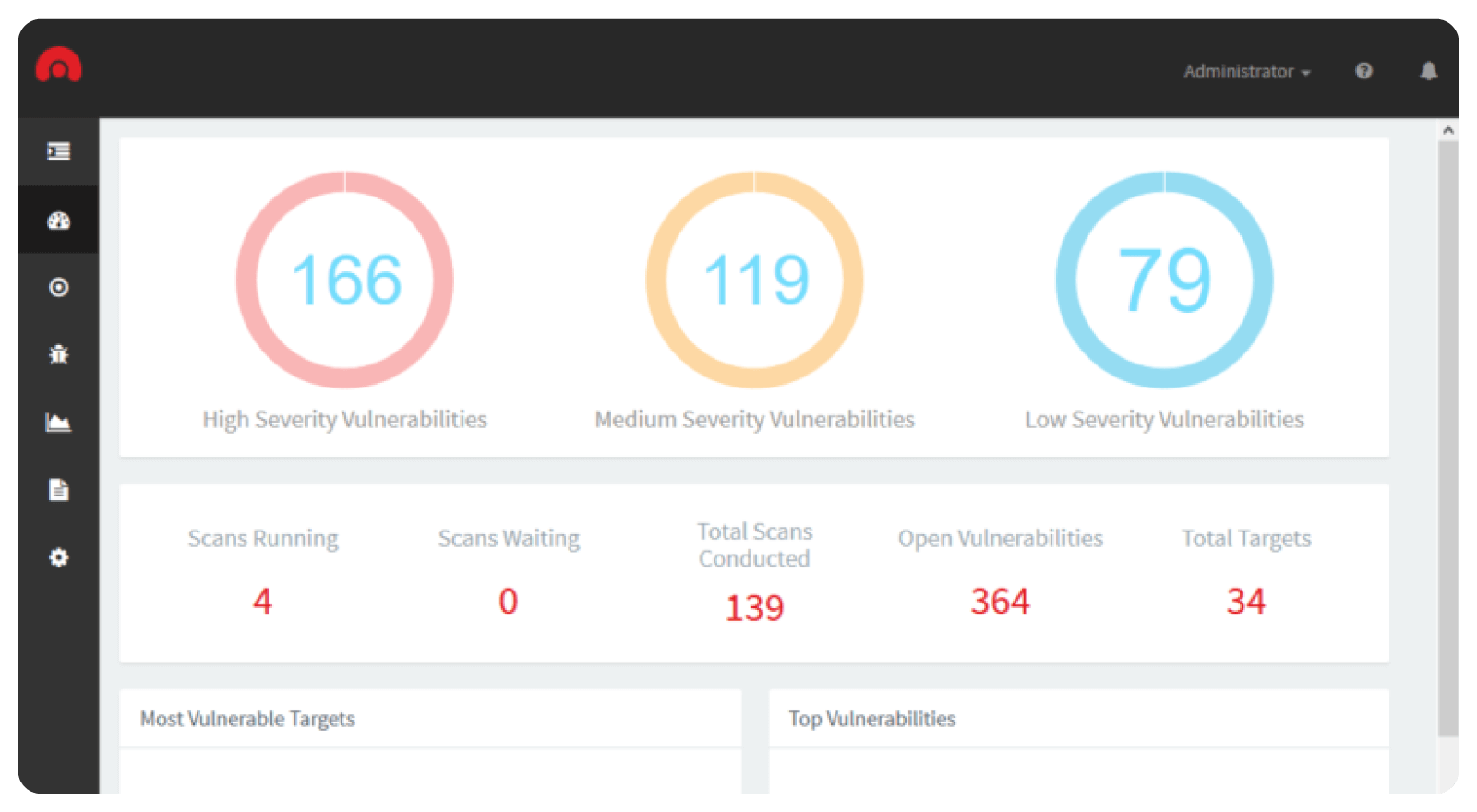
These solutions don’t overwhelm you with an unending list of potential issues. They classify vulnerabilities according to their impact and notify you accordingly. Hence, you can utilize your resources efficiently and focus on the most critical vulnerabilities first.
7. Malware scanner
A malware scanner helps you identify threats that involve malicious code. These tools help you cope with web-based threats that may include but aren’t limited to hidden backdoors, malicious redirects, phishing attempts, etc.
The tools use multiple detection methods and compare your files against known malware signatures. They analyze your code and look for suspicious file modifications.
Reliable malware scanners don’t just scan threats. They also provide you with automated cleaning capabilities. When they detect any threat, they will automatically quarantine infected files, remove malicious code, and restore compromised files to their clean state. They also provide you with detailed logs and detected threats so you can track potential changes.
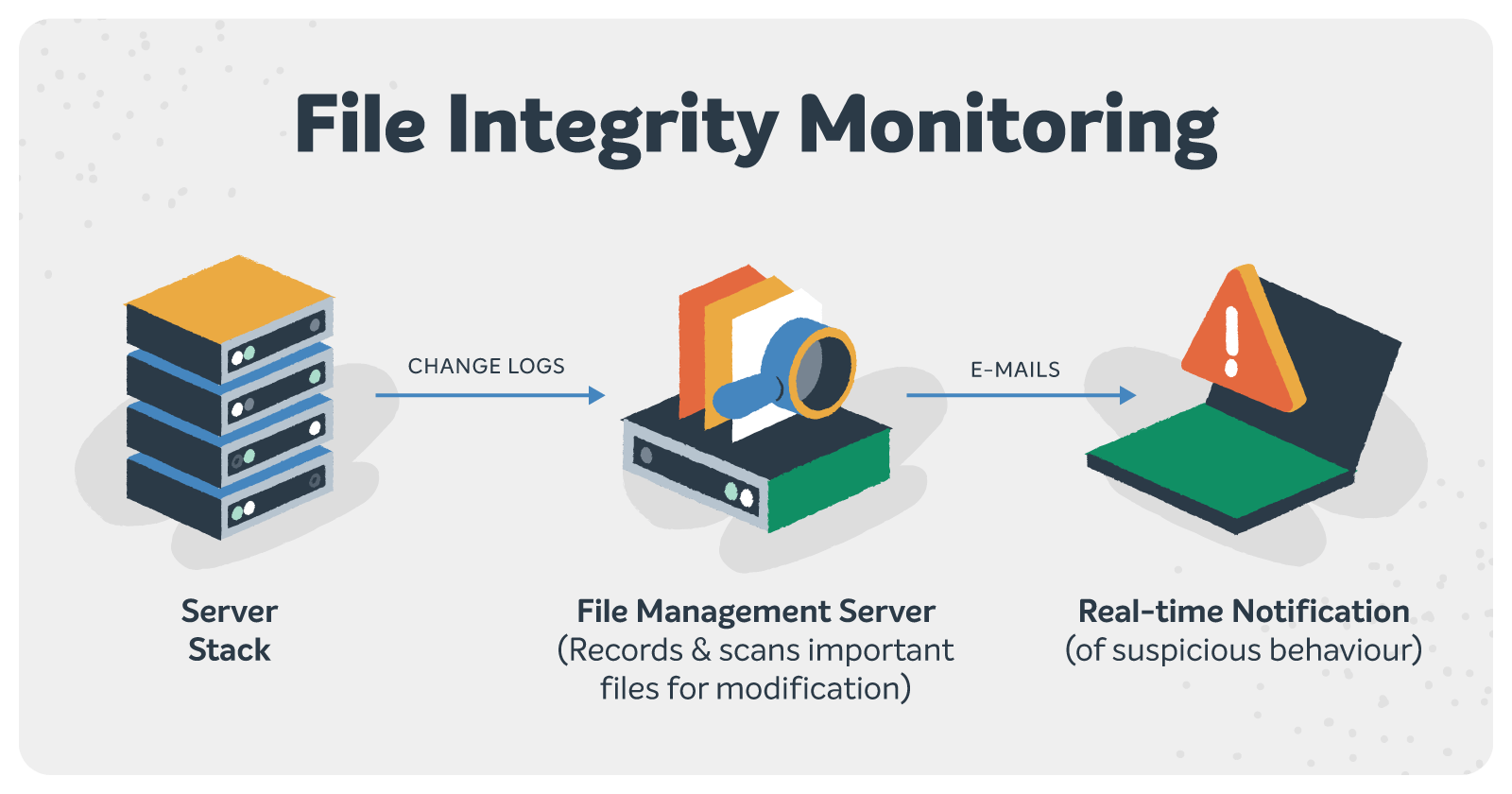
8. File integrity monitoring solution
A file integrity monitoring tool is your site’s watchful protector. It monitors the changes made to your critical files. Be it unauthorized modifications, additions, or deletions, it keeps an eye on them all. It notifies you immediately when it detects the changes that occur.

You can easily identify potential security breaches that may lead to critical incidents. You know who changed what and when. There are no false alarms here. An FIM solution keeps your website safe and makes it easier for you to ensure your regulatory compliance status.
9. DNS health checker
A DNS health checker is a useful tool that comes in handy for validating your DNS configurations. It’s a diagnostic tool that monitors the connection between your domain and the web server. It consistently checks your DNS records, keeping an eye on misconfigurations, unauthorized changes, or potential security exploits.
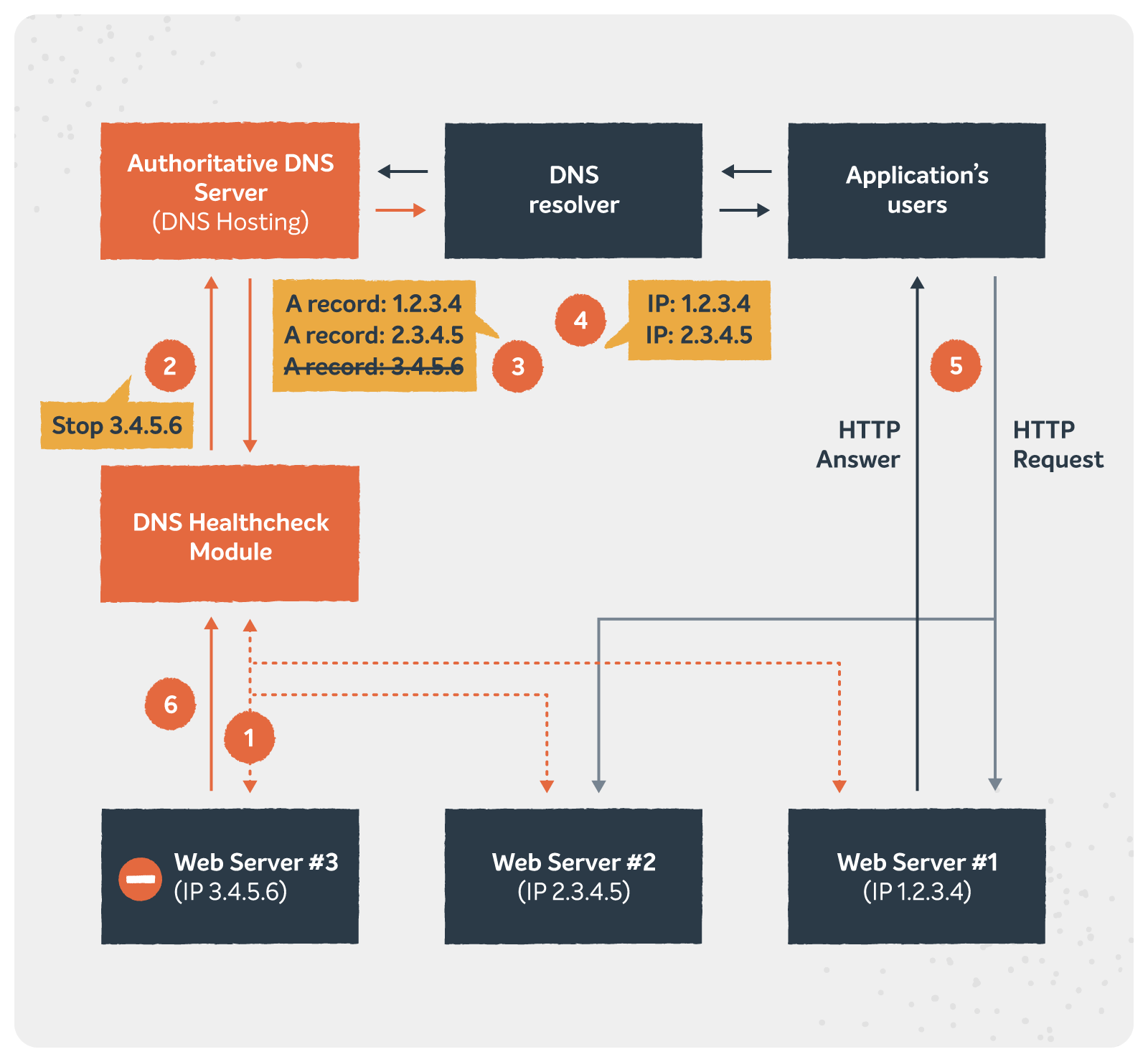
A reliable DNS health checker solution notifies you about near-expiry SSL certificates. Plus, it helps you with seamless DNS propagation across all servers. Overall, it’s a handy tool that allows you to maintain your domain’s integrity and prevent potential DNS issues.
9 website security audit best practices
You should be mindful of a few things when conducting a website security audit. The following are a few noteworthy best practices that you should consider following.
1. Conduct a penetration test
You should conduct a penetration test when conducting a website security audit. Here, you test your website’s security by trying to break in and access the stored information. You can hire an expert to conduct a penetration test or assign this task to your team. It helps you identify potential issues in your website’s security.
You start penetration testing by observing the website’s potential weaknesses. Let’s say it’s using an outdated theme or a plugin. You can find many vulnerabilities like these. Your goal is to identify them so you can exploit them in the testing phase.
The next step is the testing phase. Here, you try to exploit the issues that you discovered in the planning phase.
The third step is the reporting phase. Here, you create a detailed report of your findings, including a list of identified vulnerabilities. You also assign ranks to the issues you discovered based on the damage they can cause. Plus, you recommend viable fixes to the issues.
2. Change your password
No matter how strong your password is, you must keep changing it to keep your website secure. Compromised passwords are one of the leading causes of security breaches for websites. So, you should set a new password periodically.
It’s important to have a strong password, containing at least 12 characters. Your password should be a mix of uppercase and lowercase letters, along with numbers and special characters. You must avoid common words or predictable patterns when setting a new password for your website.
Never resort to a weak password because it’s easy to remember. Always pick a strong one and use a password manager for easy recall. To keep your website secure, you must implement temporary passwords with quick expiration times. Notify authorized personnel about the changes to avoid inconvenience in operations.
3. Leverage multi-factor authentication
Just picking a strong password and changing it periodically isn’t enough to ensure your website’s security. You must add different layers to the authentication process.
Multi-factor authentication is the way to go. It acts as an additional layer to website security that significantly minimizes the risk of unauthorized access. Even if someone has your passwords, they won’t be able to get in and access your information.
You should also have backup authentication methods in place for users who lose access to their primary authentication device. Even when you’re leveraging multi-factor authentication, you should keep an eye on unusual authentication attempts.
4. Look for essential software updates
Outdated plugins or themes are likely responsible for over 50% of website vulnerabilities. Updates don’t just fix the issues with software’s features, but they also cater to security vulnerabilities.
The use of outdated solutions, such as plugins, themes, and CMS makes you susceptible to security threats. Therefore, you should always use the latest versions.
You must have a systematic update management process in place for all software components. Create a staging environment to test software updates before installing them, ensuring they don’t compromise any functionalities. You can delay feature updates a bit, but you should never be complacent when it comes to the ones that are security-specific.
You must maintain a detailed record of all software updates. It helps you track security improvements and troubleshoot any issues after automatic updates.
5. Review user access and permissions
User access control is important to ensure your website’s security. It prevents unauthorized people from accessing your data. You set certain ground rules and allow users to access the data only when they need it to perform their roles.
Reviewing your access settings on a periodic basis is necessary, as excessive permissions, dormant accounts, and outdated access rights often cause unnecessary security risks. You should conduct regular audits of user accounts and monitor associated permission levels.
Immediately remove inactive accounts, temporary ones, and the ones that belong to former team members. For active accounts, see that your permissions align with the job roles or assigned responsibilities.
6. Ensure secure communication
Secure communication acts as the backbone of your website security. Using strong encryption is the way to go, as it keeps your sensitive data safe. You can’t just install an SSL certificate and call it a day. You must constantly monitor things to ensure that all your data transmissions remain secure.
Regular SSL configuration checking helps you identify potential loopholes in your encryption before they cause critical damage. Make sure that your pages don’t load insecure (HTTP) resources, as they can compromise a secure connection. You should also use security headers to control resource loading and prevent unauthorized data transmission.
7. Leverage secure web hosting
Settling for a subpar hosting service provider is a critical mistake. A reliable hosting service makes your website secure and ensures its performance. Your hosting service should provide you with essential security features and backup capabilities.
Even then, you should regularly review your hosting security settings. You must enable features like IP blocking for repeated failed login attempts and maintain secure FTP access protocols. Knowing this, even the most secure hosting solution requires proper configuration and regular maintenance to perform well.
8. Review third-party integrations
Third-party integrations improve your website’s functionality. However, they may also make you susceptible to security risks. Each external service you integrate requires regular assessment and monitoring. Therefore, it’s important that you maintain an up-to-date inventory of all third-party integrations.
You should document their purposes, access levels, and data-sharing agreements. Perform a regular check on their security and remove or replace integrations that show signs of security issues. External integrations can act as the weakest links to your security. So, make sure that they meet your security standards.
9. Create a website backup
Having a website backup is essential. It acts as your last line of defense against both security incidents and technical failures.
Even with all your preparedness, you shouldn’t exempt yourself from the worst-case scenarios. That is losing all important information. Having a website backup ensures quick data recovery when needed. It’s like your website’s insurance policy.
You must also test your backup restoration process periodically. A website backup is only useful when you can restore valuable data from it. So, you should run periodic recovery tests to see how quickly you can restore your website when things go wrong.
Easily conduct regular security audits for peace of mind
Ensuring the security of your website is an ongoing task. You need to be vigilant and proactive. With our recommendations, you can easily conduct regular security audits and protect sensitive information.
To keep up with constantly evolving security threats, you need to embrace the best practices and use the right tools that help you protect your data. Only through testing and careful monitoring will you be able to protect yourself from emerging security threats.
However, you shouldn’t overwhelm yourself trying to create an unbreakable fortress. Identify the vulnerabilities, rank them as per their impact, and plan your course of action.
