How to detect and remove malware from a WordPress website

It’s hard to imagine a more devastating feeling for a website owner than to find out that your WordPress website is infected with malware. Your head starts buzzing with questions like, how did my website get infected? How do I find the best plan for WordPress malware removal? And how do I make sure my website is secure in future?
While this is definitely a frustrating experience, there’s no need to panic.
In this article, we’ll provide all the necessary information on WordPress malware as well as actionable steps for you to clean up your website and keep it protected against potential, future online threats.
If you think your website has been infected or you’re only suspecting it to be so, jump to the section where we explain how to detect and remove malware from WordPress websites.
What is malware?
In simple terms, malware (malicious software) is a piece of software or a code created to damage a system or gain unauthorized access to it (be it your website, smartphone or PC).
Depending on its type, WordPress malware can do anything from adding Japanese characters to your pages’ meta descriptions to completely hijacking your website.
Most common WordPress malware infections
When it comes to the most common WordPress malware types, there are mainly four types of infections you should be on the lookout for:
Backdoor. Backdoors allow hackers to gain access to your website by exploiting outdated software, security loopholes in a code as well as default passwords. Sometimes, you can spot this malware if you see that a file name has been changed, like lok.php.
Drive-by downloads. This type of malware injects download links into your website to get your users to download a payload onto their local machine. That payload will then show a warning that the computer has been infected and provide a link to install an antivirus (which is another payload).
Pharma hacks. The pharma infection adds SPAM links to your website that lead to actual online pharma stores. Pharma links are deemed to be the most popular type of site infection and can even use conditional rules to control what the user sees making it much harder to locate.
Malicious redirects. This malware redirects users that call up your website address to a malicious website. That malicious website may also contain a payload that automatically downloads to the user’s computer.
If you want to learn more about the common WordPress malware infections, check this article.
Signs your WordPress website has been hacked
What’s tricky about malware is that it’s not always obvious your website has been infected. Some malware infections prefer to keep a low profile, which is why your site might not show any visible symptoms.
With that in mind, we’ll list the most effective ways to tell if your website has malware, from the most probable to more subtle ones.
- Your site has been flagged by Google
If you see this red screen of death when visiting your website, it means Google has either detected malware on it or have good reasons to believe so:
Such a message appears when your website is blacklisted by Google Safe Browsing which popular browsers like Google Chrome, Mozilla, Safari use to warn their users about a potential threat.
- Google Search Console sends you warnings about your website being hacked
Google can also send you warning messages and emails notifying you that your website has been infected, provided you’ve connected it to Google Search Console. These messages also give information about the suspicious URLs as well as possible attack vectors.
- Your hosting provider takes down your website
Hosting providers often search their servers for signs of malware and can suspend hacked websites to prevent a virus from spreading. There are several reasons why your website can be disabled by your hosting. That includes malicious code found on your server, Google blacklisted your domain, spam and phishing emails being sent from your server, etc.
With EasyWP MalwareGuardian, you can access comprehensive dashboard reports that provide real-time insights into your website’s security status. These reports offer detailed information about detected threats, automatic actions taken to neutralize them, and recommendations for future prevention.
By regularly reviewing these dashboard reports, you can stay proactive in maintaining your website’s security and potentially avoid hosting-related suspensions due to malware issues.
- Your customers alert you about malware
A lot of times, it’s not the site owner but the users who experience malware issues first. In that case, they might reach out to you via contact form or phone to signal that something’s wrong. For example, if you run a WooCommerce store, your users might complain that their credit cards are being hacked.
But be sure to explore all possible scenarios when a customer reports an issue. If customers report issues with receiving emails, for instance, it’s worth checking whether their email client, such as Apple Mail, is not functioning properly, rather than assuming it’s malware right away.
- You see spam search results for your website
Try Googling your brand name and see if you notice anything strange about the results. The warning signs can vary from meta descriptions containing pharmaceutical or unrelated keywords and Google indexing pages that shouldn’t exist to weird characters showing up in the search results.
- Your site takes much longer to load
Poor site performance can also be a sign of your site being infected. If your pages are suddenly taking significantly more time to load, it’s quite possible that malware is using up your server’s resources.
- You noticed your site files have been changed
If you have access to your site files, take a good look at them to see if there have been any changes. If a file has been recently modified but not by you, inspect it closely for malicious code. Also, look for files with suspicious names, for example, .aspx.
How to detect and remove malware from a WordPress site
The quickest way to check your WordPress website for malware is to run an online scan.
There’s not one but several tools that will search your website for malicious code for free. All you need is to enter a URL and hit the Scan button.
While this method is quite handy, you should also keep in mind that it might not be the most thorough one, as these tools scan only visible files and don’t account for hidden ones or database tables.
Here are 4 of the most popular free online malware scanners for websites:
- MalwareGuardian. Developed by EasyWP, MalwareGuardian is an automated malware scanning and cleaning tool designed specifically for WordPress websites. It provides continuous monitoring for malicious activities, offers fully automated scanning and cleaning with Autoclean protection, and generates comprehensive scan reports.
- VirusTotal. VirusTotal allows you to scan your website or a specific file by leveraging 70 antivirus scanners and URL/domain blocklisting services. Should VirusTotal detect malware on your website, it will also show you the infection type and if it belongs to a known botnet.
- Sucuri SiteCheck. Brought to by Sucuri, SiteCheck is another popular malware scanner. Apart from searching websites for malicious code, it also checks your website blacklist status, finds out-of-date software & plugins, and even detects security issues and anomalies.
- WordPress Security Scanner. If you’re looking for advanced WordPress malware removal, Seahawk’s WordPress Security Scanner is a powerful tool designed to fortify your website against a wide spectrum of malware threats. This scanner performs comprehensive scans of your WordPress website’s files and databases, meticulously searching for any signs of malware, vulnerabilities, or suspicious activities. Its advanced algorithms meticulously analyze the code and structure of your website to detect even the most intricate security breaches.
How to detect and remove malware with a security plugin
Time is of essence when it comes to cleaning your WordPress website from malware. The faster you react, the fewer issues you’ll have to deal with.
This is why it’s recommended to remove malware with the help of a security plugin. Not only will it help you detect malicious code more efficiently, you can also get your WordPress website up and running again in a timely manner (depending on your plugin plan and the severity of the situation).
1. MalCare (automatic malware cleanup)
Activate installs: 100,000+ (WordPress.org)
Rating: 4.1 (WordPress.org)
Pro price: from $99/year (1 site covered)
First on our list is one of the most popular malware removal plugins for WordPress called MalCare. It has both paid and free versions, although the latter one will only allow you to run scans of your websites and protect them with Malcare firewall. To get your WordPress website cleaned from malware and harden your security, a premium license is required.
The good news is you can clean your website as many times as you need in case it gets infected again in the future.
If MalCare detects malicious code on your website, the plugin will make a backup of the affected files (or database tables) and automatically clean your website.
Some of the premium Malcare features include:
- Auto-cleanups (let MalCare automatically remove malicious code from your website)
- Geo-blocking (block countries’ IP addresses with a few clicks)
- On demand scans (run a scan anytime to see the current state of your website’s security)
- Daily automatic scans (nip malware in the bud by running daily automatic scans)
- Premium Support (get faster, personalized assistance)
2. Sucuri (service-based malware cleanup)
Active installs: 800,000+ (WordPress.org)
Rating: 4.3/5 (WordPress.org)
Pro price: from $199,99/year (1 site covered)
Sucuri is a security company that provides services for scanning and cleaning your WordPress website from malware. The plugin itself is completely free allowing you to harden your security as well as search your website for common types of malware infections.
However, if your WordPress website happens to be hacked, you can either attempt removing malware manually or request a Sucuri malware removal service (requires a paid plan).
Important features of the Sucuri WordPress Plugin:
- WordPress security hardening (verify your security configurations and add a set of security rules to your website’s .htaccess file)
- Malware scanning (search your site for malicious code)
- Post-hack measures (implement a list of important measures once your site is clean)
- Sucuri firewall integration (get extra protection by connecting your website to Sucuri’s firewall, requires a paid plan)
- Core integrity check (make sure your WordPress core files are intact)
- Email alerts (stay informed of any harmful activity on your website)
3. Wordfence (service-based malware cleanup)
Active installs: 4+ million (WordPress.org)
Rating: 4.7/5 (WordPress.org)
Pro price: $99/year (1 site covered)
The Wordfence plugin is another all-in-one security plugin that offers outstanding security features. With that said, it doesn’t provide a way for you to automatically clean your website from malware. Instead, you can hire the Wordfence site-cleaning team to take care of that for you for $490 per WordPress installation.
This offer also includes a one-year premium subscription worth $99.
Important Wordfence plugin features:
- Security scanner (scan your website for malicious code)
- Wordfence firewall (keep out malicious traffic)
- Login security (protect your admin area by implementing security measures like two-factor authentication)
- Premium: Real-time IP blacklist (block all requests from known suspected IP addresses)
- Premium: Real-time firewall rule updates (protect your website from the latest attacks and security vulnerabilities)
- Premium: Real-time malware signature updates (get more accurate scanning results by leveraging thousands of malware signatures)
Remember, with EasyWP’s MalwareGuardian enabled on your site, you can enjoy robust malware protection without the need to install any additional security plugins, streamlining your site’s security management.
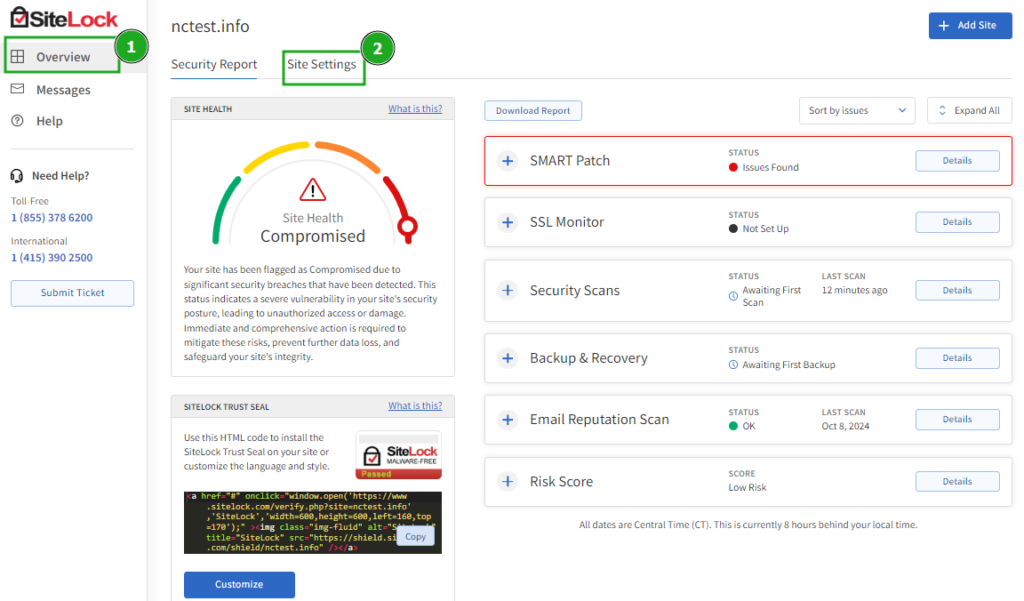
4. SiteLock from Namecheap
Active installs: Cloud-based, no plugin required
Rating: 4.5/5
Pro price: from $48.88/year
SiteLock is a comprehensive, cloud-based security solution for WordPress websites that offers protection without the need for a plugin installation. Unlike traditional security plugins that can impact server performance, SiteLock operates externally, providing robust security measures without slowing down your site.
Key features of SiteLock from Namecheap include:
- Daily malware scanning (automatically detect malicious code on your website)
- Automatic malware removal (instantly remove infected files and clean your database)
- Vulnerability patching (identify and fix security weaknesses in your site’s code)
- Website backup (protect against data loss with automatic backups)
- Trust Seal (display a badge to show visitors your site is secure)
- Continuous monitoring (get real-time alerts about potential security threats)
How to remove malware from a WordPress site manually
Removing malware manually is also an option, although only experienced WordPress users should proceed with this method. It’s no easy task to successfully detect and eradicate all malicious code if you haven’t done this before.
In the worst case scenario where your site is down and you can’t access it, you’re better off hiring a professional to get it up and running again.
Should you still want to try to do it on your own, here are the steps that will help you:
Step 1. Backup your website files and database
Before starting the cleanup, make sure to backup your entire website, including your database. There are multiple ways you can do so. For example, some WordPress hosting providers offer the snapshot feature that creates a copy of your website in a couple of clicks. You can use WordPress security or backup plugins as well.
Last but not least, you can access and download your site files via File Manager (in cPanel) or FTP/SFTP. To back up your website database, use the phpMyAdmin tool.
Don’t forget to download the .htaccess file which is an invisible one. Rename it temporarily so that you can see it on your PC.
If you have multiple sites on the same server, repeat all the steps for each of them to prevent cross-contamination.
Step 2. Examine and clean your database
Now that you have a backup of your database, you can examine it via phpMyAdmin. Look through the database tables and search for suspicious content like spammy keywords and links. Some potentially harmful PHP functions include base64_decode, gzinflate, error_reporting(0), and shell_exec.
If you think that your website is infected with phishing, take a good look at the wp_posts and wp_pages tables. Another important table to check is wp_options as a lot of times it’s infected as well.
Try removing suspicious content and see if the website is still working. If not, you can reupload your database from the backup and ask for assistance from your webmaster.
It’s important that the database is clean before proceeding to the next step.
Step 3. Reinstall WordPress
First, double check if the website backup is complete. After that, remove all site files in public_html save for server ones. You can now reinstall WordPress either by using cPanel or manually.
Step 4. Reset passwords
Connect the new installation to your website database by copying the database credentials from the old wp-config.php to the new one. If you’ve added customizations via CSS, PHP or JS files, you’ll need to copy your code over to the new installation. Provided that you’re 100% sure there’s no malicious code there.
Log in to WordPress and make sure to change passwords for all existing users.
If you see any suspicious users you didn’t create, chances are your database is still compromised. It’s better to contact a professional in this case.
Step 5. Reinstall plugins and themes
Download fresh copies of your plugins and themes from the WordPress repository or from the marketplaces where you’ve purchased them.
Step 6. Upload your images from the backup
Carefully examine each folder in wp-content>uploads for suspicious files. There should be only the images that you’ve uploaded into WordPress, no PHP or JS files.
After the check is done, transfer the images to the corresponding folder of your new installation via File manager or FTP/SFTP.
Step 7. Install a security plugin and run a scan.
Get a security plugin of your choice to harden your WordPress security and be in the loop of any suspicious activity on your WordPress website. Run a scan to see if there are any signs of malware left after the cleanup.
Step 8. Remove security warnings
If your website has been infected for some time, it’s most likely flagged by search engines and web hosts. To take off malware warnings from your website, request a review through the Search Console when all malicious code is gone.
How to protect your WordPress website from malware
While the WordPress core is completely secure thanks to the great care put into it by its developers, it’s third-party plugins and themes that make this CMS such a popular target of online attacks. Reason being their code might contain security loopholes rendering your website prone to online attacks.
And since WordPress is powering roughly 43% of the Internet, once a security vulnerability is discovered by hackers, thousands of websites become a playground for malicious actions. With that said, there are other important factors that account for a huge portion of WordPress security breaches. So here are some important security tips that will help you keep your WordPress website secure:
- Minimize human error. Human error is a huge reason behind security breaches in all scenarios where credentials are involved. Usually, it comes down to having a weak password (remember brute force attacks), sharing sensitive information online, or simply falling for a phishing link or website. Once your credentials are compromised, it’s a matter of time before your website is infected with malware.
- Keep your WordPress up-to-date. To put it short, if you’re running a previous WordPress version, it means it has known vulnerabilities. Every WordPress update comes with notes that state what security issues have been patched. Hackers read those to then search and target websites that haven’t been updated.
- Avoid using outdated plugins and themes. Keeping your plugins and themes up-to-date is one of the basic requirements for your website to be secure. According to ScanWP, 52% of WordPress vulnerabilities relate to plugins.
- Say no to nulled plugins. A nulled plugin is a hacked premium plugin that can work without a license while providing a certain amount of premium features. Usually, nulled plugins have considerable security issues and can even contain malware.
- Choose a reliable hosting provider. Sadly, not all hosting providers offer the required level of security for your website to be protected from the server side. This is why we highly recommend that you choose hosting providers designed for WordPress specifically.
- Keep a security plugin activated. Using a security plugin (even a free one) will allow you to keep an eye on the state of your security by running regular scans, enable firewall for better protection and implement additional measures like Two-factor authentication.
- Consider using HackGuardian. This free security tool from EasyWP switches your WordPress file system to a partial, read-only mode, providing robust protection against unauthorized modifications. With HackGuardian, you can easily toggle between protected and normal modes directly from your dashboard, allowing for seamless updates and changes when needed while maintaining strong security.
Final thoughts
We hope this guide helps you to identify all the types of malware that you may come across and successfully remove malware from your WordPress website so you can get it back up and running again.
With WordPress being a popular platform – we expect to see it power 50% of all websites by 2025 – among business owners and hackers alike, we strongly recommend that you have your website’s security at the top of your priorities. Even the most basic security measures can shield you from the majority of online attacks keeping your business safe and clients happy.
What is your approach to keeping your website secure? Let us know in the comments or on Twitter.
And if you want more tips on security, check out our article about making WordPress more secure.
